Jenkins is the leading open-source automation server for developers looking to build applications in a continuous integration/continuous delivery (CI/CD) pipeline. If you are a developer using Jenkins who also cares about application security, you may have questions. How secure is the code I just pushed to an online repository? Is there a way to find out without juggling between development tools? Is it possible to integrate this type of security into the Jenkins pipeline?
The answer is “Yes.” All of this can be achieved using the HCL AppScan plugin for Jenkins, effectively integrating security into the CI/CD pipeline. Once the plug-in is downloaded, installed, and configured with AppScan on Cloud (ASoC), application security can become an easy priority to manage.
For starters, the plug-in empowers developers with the tools to perform checks for security vulnerabilities while coding and building their projects, and without the need to move back and forth from Jenkins to ASoC. And AppScan on Cloud supports a wide range of languages when used to perform Static Application Security Test (SAST) scans and this capability can be leveraged when using the plug-in.
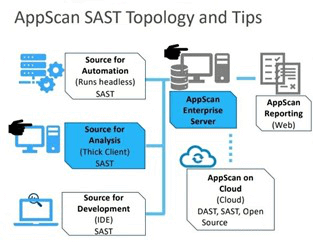
The plug-in also allows you to benefit from the Machine Learning capabilities of AppScan like Intelligent Finding Analytics (IFA) and Intelligent Code Analytics (ICA), which provide results that are based on actionable issues and Fix groups.
IFA is a powerful machine-learning technology that does much of the triage work for you by, among other things, filtering out false positives and by grouping findings that can be remedied by a fix in one code point. More on IFA can be found in this article.
In addition, static analysis scans make use of Intelligent Code Analytics (ICA). ICA automatically discovers new application programming interfaces (API) and assesses them for security impact. Through ICA, all third-party API and frameworks are reviewed and assigned the right security impact. This allows for more complete scan results. Read this article to learn more about ICA.
When setting up your scans, you can configure the build to fail based on the specified security results such as the number of high severity vulnerabilities found. And you can reduce scan time by choosing a balance between speed and issue coverage. Optimized scans omit tests defined in the test policy for less severe or less likely vulnerabilities based on ongoing statistical analyses. Read more about test optimization here.
Watch this video for a demo on HCL AppScan On Cloud: Jenkins Integration.
Turn your “DevOps” into “DevSecOps” in Jenkins using the HCL AppScan plugin. For more information visit the HCL AppScan website to learn more or use this link to begin your free 30-day trial of HCL AppScan On Cloud.



